
Researchers at ESET have uncovered a cyberespionage campaign targeting Tibetans across several countries, including India, Taiwan, Hong Kong, Australia, and the United States. Since September 2023, the China-aligned group known as Evasive Panda has been using sophisticated cyberattacks to spy on Tibetans by exploiting their interest in the Monlam Festival, a significant religious event for Tibetan Buddhists.
The attackers compromised the website of the Monlam IT Research Centre, an India-based developer of Tibetan language translation software, to distribute trojanized versions of this software. According to ESET, this move allowed the attackers to deploy malware called MgBot and a newly identified backdoor dubbed Nightdoor on victims’ computers, targeting both Windows and macOS users.
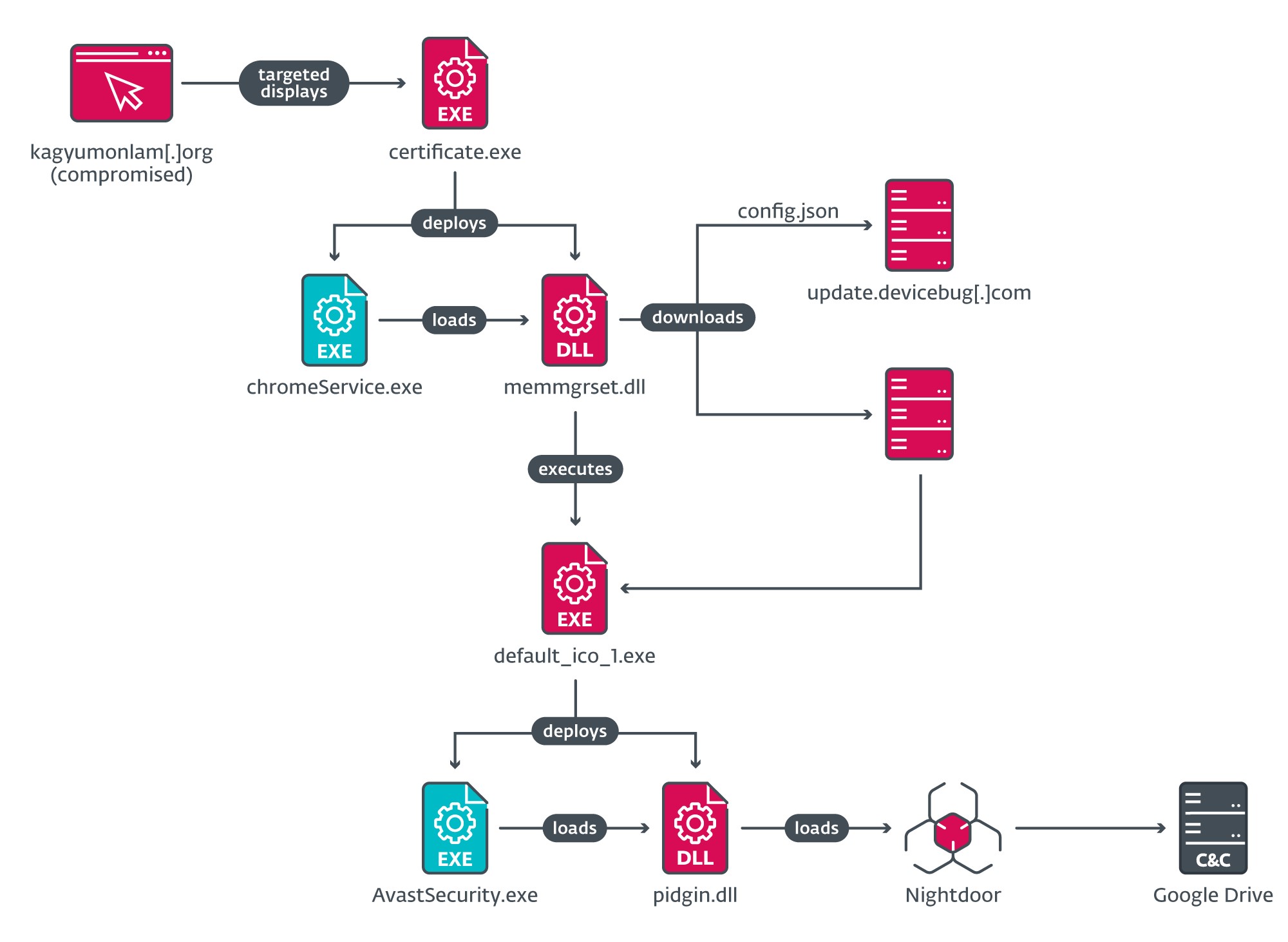
ESET’s discovery in January 2024 highlighted the severity of the attack, particularly focusing on the Kagyu International Monlam Trust’s website. This organization, dedicated to promoting Tibetan Buddhism internationally, hosts the annual Kagyu Monlam Festival in Bodhgaya, India. The Georgia Institute of Technology was also mentioned as one of the targeted entities, underlining the global reach of this cyberespionage effort.
Anh Ho, an ESET researcher, shed light on the attackers’ tactics, mentioning that Evasive Panda utilized a range of malicious tools, including the newly added Nightdoor backdoor, to infiltrate networks in East Asia.
“The Nightdoor backdoor, used in the supply-chain attack, is a recent addition to Evasive Panda’s toolset. The earliest version of Nightdoor that we’ve been able to find is from 2020, when Evasive Panda deployed it onto the machine of a high-profile target in Vietnam,” Ho explained.
Evasive Panda, also known as BRONZE HIGHLAND or Daggerfly, has been active since at least 2012 and is known for its cyberespionage activities targeting various regions, including mainland China, Hong Kong, Macao, and beyond.
The group’s custom malware framework and sophisticated techniques, such as adversary-in-the-middle attacks to hijack software updates, have posed significant threats to government entities and organizations within and outside of China.
For more technical information about the latest malicious campaign of the Evasive Panda group, check out the blogpost “Evasive Panda leverages Monlam Festival to target Tibetans” on WeLiveSecurity.com.






